Design
Dell Technologies (Dell) Container Storage Modules (CSM) for Authorization design
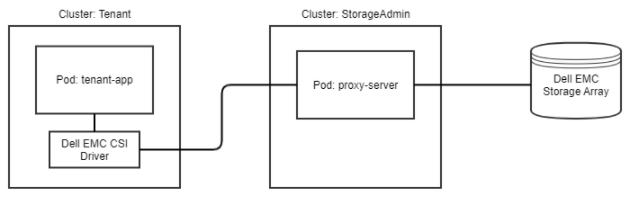
The following diagram shows a high-level overview of CSM for Authorization with a tenant-app that is using a CSI driver to perform storage operations through the CSM for Authorization proxy-server to access the a Dell storage system. All requests from the CSI driver will contain the token for the given tenant that was granted by the Storage Administrator.
| Feature | PowerFlex | PowerMax | PowerScale | Unity XT | PowerStore |
|---|---|---|---|---|---|
| Ability to set storage quota limits to ensure k8s tenants are not overconsuming storage | Yes | Yes | No (natively supported) | No | No |
| Ability to create access control policies to ensure k8s tenant clusters are not accessing storage that does not belong to them | Yes | Yes | No (natively supported) | No | No |
| Ability to shield storage credentials from Kubernetes administrators ensuring credentials are only handled by storage admins | Yes | Yes | Yes | No | No |
NOTE: PowerScale OneFS implements its own form of Role-Based Access Control (RBAC). CSM for Authorization does not enforce any role-based restrictions for PowerScale. To configure RBAC for PowerScale, refer to the PowerScale OneFS documentation.
CSM for Authorization consists of 2 components - The authorization sidecar, bundled with the driver, communicates with the Authorization proxy server to validate access to Storage platforms. The authorization sidecar is backward compatible with older Authorization proxy server versions. However, it is highly recommended to have the Authorization proxy server and sidecar installed from the same release of CSM.
NOTE: If the deployed CSI driver has a number of controller pods equal to the number of schedulable nodes in your cluster, CSM for Authorization may not be able to inject properly into the driver’s controller pod. To resolve this, please refer to our troubleshooting guide on the topic.
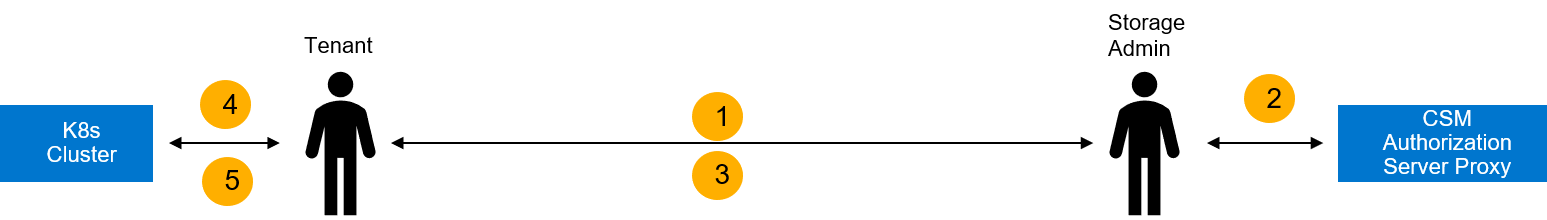
The CSM for Authorization CLI can be executed in the context of the following roles:
Storage Administrators can perform the following operations within CSM for Authorization
Tenants of CSM for Authorization can use the token provided by the Storage Administrators in their storage requests.
Dell Technologies (Dell) Container Storage Modules (CSM) for Authorization design
Methods to backup and restore CSM Authorization
Configure CSM Authorization
Dell Technologies (Dell) Container Storage Modules (CSM) for Authorization CLI
Troubleshooting guide
Dell Container Storage Modules (CSM) release notes for authorization